Network Enumeration Using Nmap: A Beginner’s Guide – Part 2
Admin
August 3, 2024

In the first part of this series, we explored the critical role of network enumeration in cybersecurity, emphasizing its importance in understanding the devices and services on a network. One of the most powerful tools for this task is Nmap (Network Mapper), an open-source tool used for network discovery and security auditing. We started by highlighting the basics of Nmap, comparing it to an airport scanner that searches for hidden objects, except Nmap searches for open ports and services on computers. We then dived into host discovery, the initial step in network enumeration, where Nmap provides methods for identifying active devices on a network by scanning network ranges, lists of IP addresses, or multiple individual IPs.
The process included discovering live hosts without scanning ports using the -sn option and saving the results in various formats (-oA). We also explored how to filter and extract IP addresses from the output, and discussed the less common but useful method of scanning specific lists of IP addresses. Additionally, we covered the flexibility of Nmap in handling multiple IP addresses, emphasizing the importance of disabling ARP ping to ensure ICMP echo requests are used for ping scans.
We will delve into the intricacies of port scanning, exploring how Nmap identifies open ports and services running on target hosts. We will also cover service enumeration, which helps determine specific details about the services identified during the scan. Furthermore, we will introduce the Nmap Scripting Engine (NSE), a powerful feature that allows for advanced network discovery and vulnerability detection through custom scripts. Finally, we will discuss various techniques for evading firewalls and Intrusion Detection Systems (IDS), ensuring our scans are stealthy and less likely to be detected. Stay tuned for an in-depth exploration of these advanced Nmap functionalities.
Open Ports, Service version, scripting Scanning
When scanning hosts and ports with Nmap, we will obtain crucial information about the network environment. The scan will identify open ports and the services running on those ports, providing insights into the accessible entry points of the target hosts. Additionally, Nmap will gather detailed service information, including the type of service and the version number, which is vital for assessing potential vulnerabilities and ensuring that services are up to date. Furthermore, Nmap can also deduce the operating system (OS) of the target hosts based on the responses received during the scan. This comprehensive data is essential for creating an accurate network map and developing effective security strategies.
When scanning ports, you will come across 6 responses:
- open – meaning TCP/UDP connection established
- closed – the packet responded with RST( reset ) hence closed
- Filtered – Nmap could not correctly identify open | closed
- Unfiltered – The port is accessible but cannot be identified if it is open | closed
- open | filtered – If no response from the port, Nmap sends this.
- closed | filtered – only occurs on IDLE scanning and can not be identified

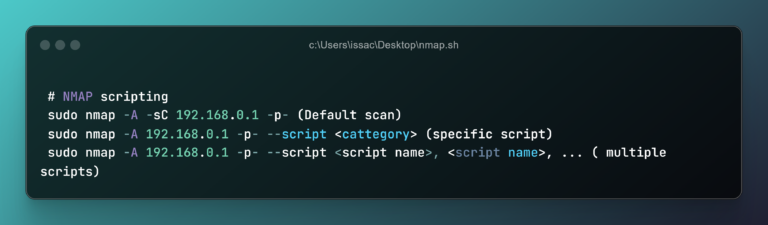
when performing version scanning we use -sV

to use nmap scripting engine (NSE), we can use -sC (script)