Network Enumeration Using Nmap: A Beginner’s Guide – Part 1
Admin
July 28, 2024
Network enumeration is a critical part of cybersecurity, helping professionals understand the devices and services on a network. One of the most powerful tools for this task is Nmap (Network Mapper). In this post, we’ll cover the basics of Nmap and how to use it for various network enumeration tasks, including host discovery, port scanning, saving results, service enumeration, using the Nmap Scripting Engine (NSE), and evading firewalls and intrusion detection systems (IDS).
What is Nmap?

Nmap is an open-source tool used for network discovery and security auditing. It can quickly scan large networks to determine which hosts are up and what services they are offering. Let’s dive into how to use Nmap for different tasks.
“Think of Nmap as a ‘scanner’. It is like those large scanning devices at airports that you walk through in order to find hidden metal objects on your person. However, Nmap isn’t looking for metal objects on people, but is looking for open ports and services on computers.”
Gordon “Fyodor” Lyon
Host Discovery - Nmap
Host discovery is the first step in network enumeration, involving identifying active devices on a network. Nmap provides several methods for discovering hosts, whether you’re scanning a network range, a list of IP addresses, or multiple individual IPs. Let’s explore these methods.
- Scanning Network Range

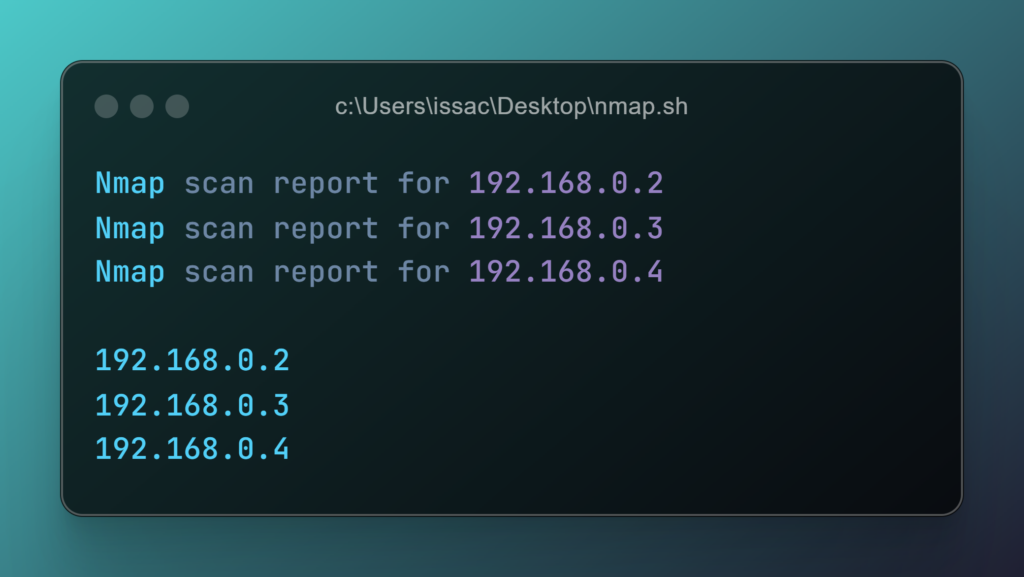
We are trying to discover live hosts without scanning ports (-sn) and saving them in all formats (-oA) provided by the tool. the formats are:
- Normal output (-oN) with file extension .nmap
- Greapable Output (-oG) with file extension .gnmap
- XML output (-oX) with file extension .XML
Furthermore, we are trying to pipe the output by
Filtering the output only to include lines containing the word “for” (this is common in Nmap’s output lines indicating a host’s IP address).
Cuts the filtered output, using a space (‘ ‘) as the delimiter, and extracts the fifth field. This is typically the IP address in Nmap’s “Nmap scan report for …” lines.
you will be having the bellow output
2. Scanning IP List
It is unlikely that you are presented with an IP list by the client when performing a Network scan, but in the scenario, you are provided with it, this is how you incorporate it within the tool

3. Scanning Multiple IP’s
When you need to scan multiple IP addresses, Nmap provides several flexible options. You can specify multiple IP addresses directly in the command line, use a range of IPs, or input a list of IPs from a file. Let’s explore these methods in detail.
- Scanning Multiple IPs Directly
- Scanning a Range of IPs
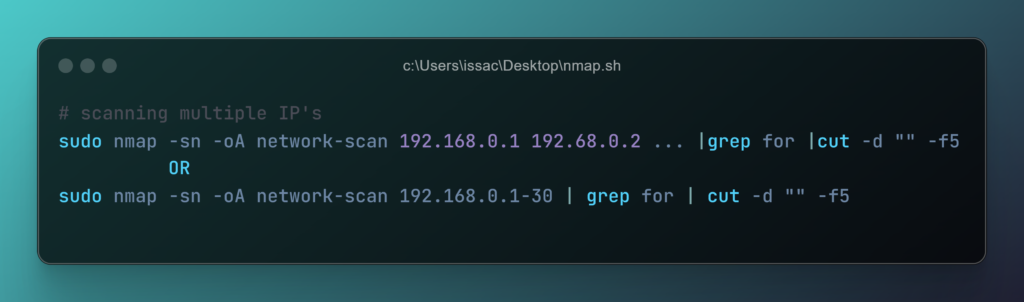
If we disable the port scanning argument (-sn), Nmap automatically resorts to performing a ping scan using an ICMP echo request (-PE). This means that instead of scanning for open ports, Nmap sends ICMP echo requests to the target hosts to check if they are up and running. The scan determines that a host is alive only when it receives an ICMP echo response from the target. However, there is another issue to consider. By default, Nmap uses ARP ping scans on local networks because they are more reliable and faster. Unless we explicitly disable the ARP ping scan, Nmap will continue to use ARP ping instead of ICMP ping. To ensure that ICMP ping is used, we must disable ARP ping with the appropriate argument. This step is crucial when we need to bypass local network limitations or when working in environments where ARP requests are filtered or blocked.

In the next blog, we will delve into the intricacies of port scanning, exploring how Nmap identifies open ports and services running on target hosts. We will also cover service enumeration, which helps determine specific details about the services identified during the scan. Furthermore, we will introduce the Nmap Scripting Engine (NSE), a powerful feature that allows for advanced network discovery and vulnerability detection through custom scripts. Finally, we will discuss various techniques for evading firewalls and Intrusion Detection Systems (IDS), ensuring our scans are stealthy and less likely to be detected. Stay tuned for an in-depth exploration of these advanced Nmap functionalities.
Conclusion
In this blog, we explored the fundamental aspects of Nmap for host discovery, a critical step in network enumeration. We started with scanning a network range, where we learned how to identify active devices within a subnet efficiently. Then, we delved into scanning an IP list, demonstrating how to use a predefined set of IP addresses for targeted host discovery. Lastly, we covered scanning multiple IPs directly, showcasing the flexibility and power of Nmap in handling various host discovery scenarios. By mastering these techniques, you can effectively map out networked devices, paving the way for more detailed and comprehensive network analysis in subsequent stages. Stay tuned for our next blog, where we’ll dive deeper into port scanning, service enumeration, the Nmap Scripting Engine (NSE), and advanced evasion techniques.